7.6.2. System Security¶
NexLog DX-Series Recorder provides options to allow recorder administrators to fine tune the recorder’s security policies which are configured from the Security: System Security NexLog DX-Series page.
7.6.2.1. General¶
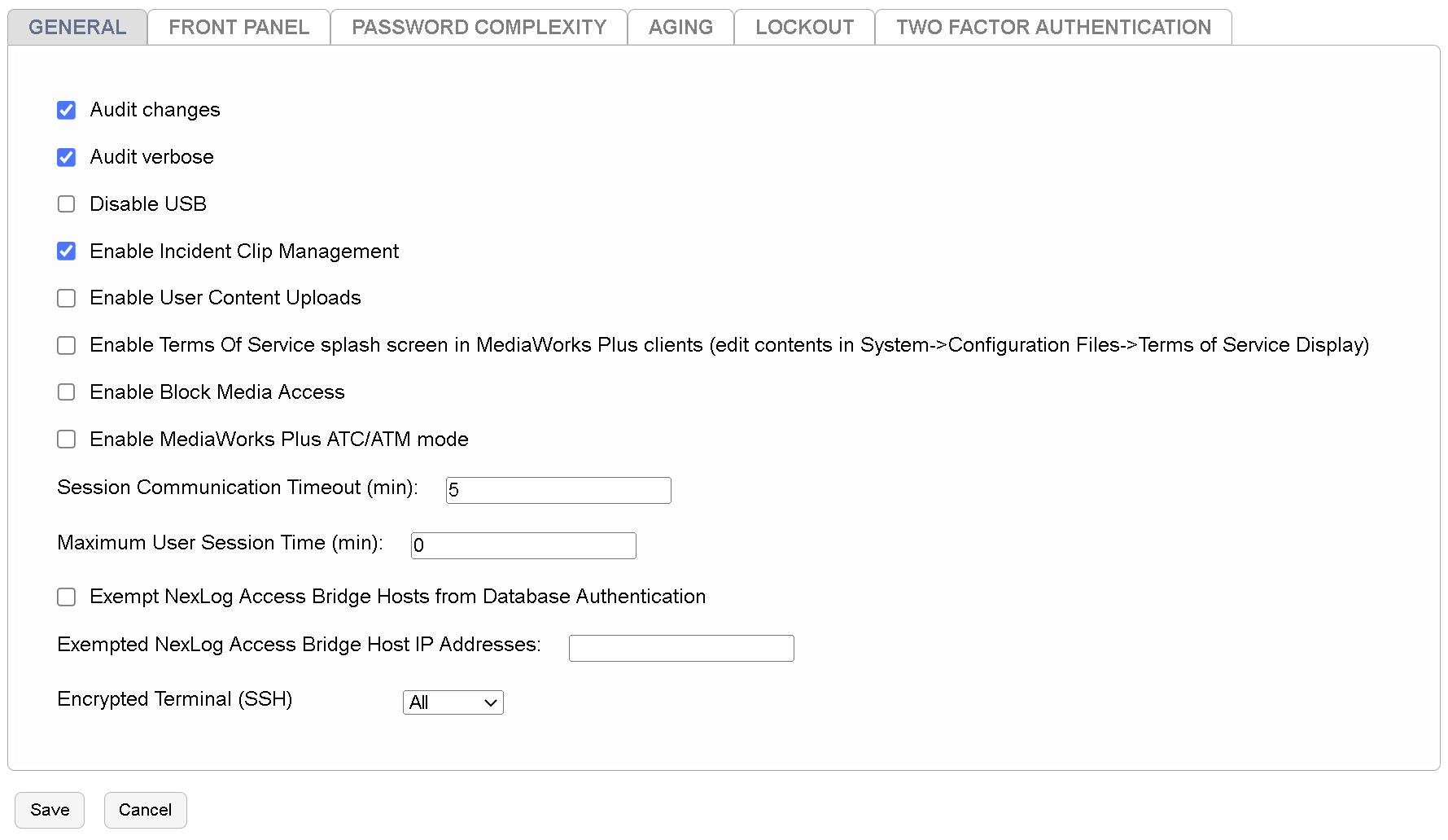
Fig. 7.115 General System Security Settings¶
- Audit Changes
If this option is enabled, then any configuration changes made via NexLog DX-Series Configuration Manager, Front Panel, or the SOAP Service will result in Audit event entries being placed in the audit history table. The audit history can be viewed by visiting the Alerts and Logs: Audit History Setup page.
- Audit Verbose
To have an effect, this option requires “Audit Changes” to also be enabled. If enabled, then the difference between the previous state and the new state will be stored along with the audit entries in the audit history table and visible for comparison. This information can be viewed by clicking on the audit event on the audit history page.
- Enable Incident Clip Management
This enables the Incident Clip Management feature in MediaWorks DX. This feature allows users to non-destructively splice or join analog calls that were inappropriately split or merged based on VOX hold settings. It is disabled by default so that administration can decide if this feature meets the needs of your site’s policies. For more information on its use, see the MediaWorks DX manual.
- Enable User Content Uploads
If enabled, allows a user to upload media to a NexLog DX-Series recorder channel, and use that media for incidents, evaluations, or general playback.
License Required
This feature must be licensed to be used. Contact your Eventide Communications Dealer for assistance.
Once enabled, create a new user group, and assign it the permission
Security Objects → Client Software → USER_CONTENT_UPLOADS.- Enable Terms Of Service splash screen in MediaWorks DX
A custom Terms of Service splash screen can be shown at login time for all users by enabling this. To configure the text for this, navigate to System Settings: Configuration Files and edit the file named Terms of Service.
- Enable Block Media Access in MediaWorks
Allows an Admin or user with the appropriate permission the ability to prevent certain user groups from accessing a recording. Once enabled, the option can be found in the right-click context menu of MediaWorks DX.
- Enable MediaWorks DX ATC/ATM mode
Makes changes to MediaWorks DX to suit the needs of Air Traffic Control and Air Traffic Management sites. Enables the use of Impounds and Quarantines.
- Session Communication Timeout (min)
If the recorder loses contact with a current client session, it will require a new log in at reconnection from that session after this many minutes.
New in version 2024.1.
- Maximum User Session Time (min)
If this is enabled, it will automatically close any Configuration Manager or MediaWorks sessions based on the value that has been set. So for example, if it is set to 60 minutes, a user will be signed out after 60 minutes regardless of whether or not they were active in their session.
To disable it, you can set the value to 0.
- Exempt NexLog Access Bridge Hosts from Database Authentication
This is for a very specific scenario involving NexLog Access Bridge (NAB) and Single Sign-On. If you have a NAB host that is not on the domain and the configured NAB sources have Single Sign-On enabled, they will be unable to connect. (Note that the inverse works fine, SSO Host, non-SSO Source.) In this particular case, the database authentication on the NAB source can be configured here to be bypassed when the request comes from a specific IP address or list of IP addresses. You can enter the IP addresses of the non-SSO Hosts here, comma delimited if there is more than one. (E.G. 193.57.164.242, 176.53.92.53)
- Encrypted Terminal (SSH)
The SSH terminal is only used by Eventide Service personnel to assist with diagnostics. Off by default. Only change this setting if asked to by an Eventide Service engineer.
7.6.2.2. Front Panel¶
- Desktop Mode
If enabled, the front panel interface can provide an experience similar to MediaWorks DX.
- Front Panel Login Required
If disabled, the Recorder’s Front Panel will be usable without first logging in. If enabled, users will need to supply login credentials in order to view or use the Front Panel. Normally this would only be disabled if the recorder is physically secured, for example by being in a locked rack or in a locked room. The Front Panel auto-login user determines which user account is automatically logged in if “Front Panel login required” is disabled. When Front Panel Login requires is disabled, there is no way to log in to the front panel as any user other than the auto-login user other than first enabling Front Panel Login Required in setup.
- Front Panel auto-login user
The user that will be automatically logged on. Many installations with high security requirements change the auto-login user to an unprivileged user that can just monitor channel activity.
- Enable Screen Dim
If enabled, the front panel’s LCD touchscreen will automatically adjust its brightness after the number of seconds specified in Idle Seconds. The screen will dim to the percentage specified in Dim Level. The default setting when enabled is to dim to 75% after 300 seconds. Setting Dim Level to 0 will turn the display off.
- Front Panel Landing Page
This setting controls the default page displayed on the front panel after login, or activity timeout. The default setting is Info
7.6.2.3. Password Complexity¶
This section configures restrictions on NexLog DX-Series passwords. If the “Enable Password complexity” option is disabled, then the only requirement on user passwords is that passwords contain at least one character so trivial passwords such as 1 are allowed. If this option is enabled, further restrictions can be applied. Note that password complexity constraints are enforced at password creation or modification time.
Newly configured password constraints will not have any effect on existing user passwords until the users attempt to change their password. When enabled, this option enforces basic “no dictionary words” password complexity constraints. In addition, additional configurable constraints can be enabled. Password complexity changes the configurable password restrictions are configured as follows:
- Minimum Length
The minimum total number of characters a password must contain
- Minimum Digits
The numerical characters 0-9 are considered digits. If this setting is greater than zero, then any password must contain at least that many digit characters to be allowed.
- Minimum Lowercase Characters
Any password must contain at least this number of lowercase characters (a-z)
- Minimum Uppercase Characters
Any password must contain at least this number of uppercase characters (A-Z)
- Minimum Special Characters
Special Characters are the non-numeric, non-alphabetical characters that are available on the keyboard and result in a glyph being entered. For example, !@#$%^&*() are all Special Characters, but the CTRL key is not since it does not result in the insertion of a glyph when pressed. This setting indicates the minimum number of special characters that a password is required to contain.
New in version 2024.1.
- Minimum Different Positions Of Characters From Old Password
If a password change attempt is made, then the new password will need to have characters changed in at least as many positions as the value that is set. This only applies to non-admin users.
7.6.2.4. Aging¶
The Password Aging sub header provides configuration options for the “Aging” or “Time Limiting” of passwords. If this option is enabled via the “Enable Password Aging” checkbox, users the system will require that users change their password on a certain configured schedule to continue to access the system. The configurable options are:
- :Maximum password age:After this specified number of days have elapsed since the
user last changed their password, they will be required to change it again. For example, if this option were set to 7, users would be required to choose a different password each week. If a user’s password ‘expires’ and has not yet been changed, then if the user attempts to log in to NexLog DX-Series via the web Configuration Manager or other clients, the only option they will have available to them is “Change Password”. They will not be able to utilize other client functionality until they successfully complete password modification.
- Minimum password age
If this option is set to a value greater than zero, it configures a time period after which a user changes their password in which they are prevented from changing their password again.
- Warn Before Password Expires
Will warn the user this many days before a password change is required.
- Reject Previous Passwords Including Current
Remember historical passwords and don’t allow them to be re-used. If set to a value greater than zero, this option will prevent a user from reusing a recent password. For example, if set to three, a user required to change their password every three months could not simply rotate between ‘password1’ and ‘password2’. Normally this option would only be used in conjunction with the Minimum Number of Days feature described immediately above. Otherwise, users could simply change their password several times quickly to clear out the configured “recent history” list to get around the security requirements.
7.6.2.5. Lockout¶
Clicking the “Lockout Settings” sub header provides configuration settings allowing user accounts to be temporarily “locked out” upon presentation of an invalid password. This can be used to prevent unauthorized personnel from gaining access to the recorder by using automatic scripts to attempt many passwords very quickly. To enable this option, check the “Enable Account Lockout” Checkbox and configure the two fields below:
- Lock After Failed Attempts
The number of unsuccessful passwords that must be entered in order for a user’s account to enter the locked out state
- Lock Duration
The number of seconds a user’s account remains in the lockout state once the threshold above is met.
None of the settings on this NexLog DX-Series Configuration Manager page will take effect until the ‘Save’ button is pressed.
7.6.2.6. Two Factor Authentication¶
Two Factor Authentication (2FA), also known as Multi-Factor Authentication (MFA), enables a second piece of information that must be entered to log in to an account. This second factor is used in conjunction with your username and password.
2FA ensures that a user logging in is really who they say they are by requiring at least 2 of 3 common factors:
Something you know (password)
Something you have (smart card, token, PIV, CAC)
Something you are (fingerprint, retina scanner)
NexLog DX-Series natively uses something you know and something you have. Something you are and can be implemented externally by integrating with Active Directory.
In NexLog DX-Series, the first factor is your username and password (something you know). The second factor (something you have), is a Time-based, One-Time Password, or TOTP.
7.6.2.6.1. TOTP¶
A Time-based, One-Time Password (TOTP) is a randomly generated token or code, that must be entered after logging in with your username and password.
As the name suggests, a TOTP token is only valid for a short period of time. The token is typically generated by a password manager or smartphone app. You may have used this second factor before without knowing it. Some online services (e.g., financial institutions) will send a random code to your mobile phone when logging in from an unknown location.
When this option is enabled for a user’s account, a secure randomly generated secret will be provided to the user. The secret is then applied to their chosen authenticator for token generation. The time on the generation device should match that of the recording system.
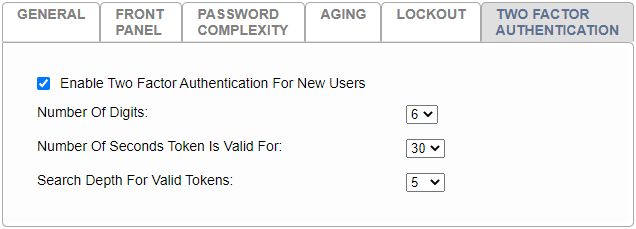
Fig. 7.116 TOTP Configuration¶
- Enable Two Factor Authentication For New Users
Enable this option to enforce 2FA enrollment on every new user account created after enablement. Disabling this option will not unenroll accounts from 2FA, it will only allow new users to be created without it.
- Number of Digits
This value controls the number of digits expected for user validation. The default setting (6), is the most commonly used in token generation applications. This value should only be changed if your token generation application supports it.
- Number Of Seconds Token Is Valid For
This value controls how often a token is cycled, or its validity period. The default value (30), is the most commonly used in token generation applications. This value should only be changed if your token generation application supports it.
- Search Depth For Valid Tokens
This value controls the allowed time drift for a token and is used along with the token validity period. The default setting is 5. If the depth and validity period are both set to their defaults, then a token generated within the previous or next 2 min 30 seconds would be valid.
(30 seconds) * (5 depth) = 150 seconds
7.6.2.6.2. TOTP Generators¶
This list of TOTP token generators is provided for your convenience. The products listed are neither supported nor affiliated with Eventide Communications LLC or NexLog DX-Series.
7.6.2.6.2.1. Desktop TOTP¶
7.6.2.6.2.2. Mobile TOTP¶
7.6.2.6.2.3. Hardware TOTP¶
Hardware tokens used for NexLog DX-Series must support a programmable secret.